How To: Wireless Network Encryption
Setting Up Wireless Network Encryption Between a Macintosh and a Non-Apple Transmitter
So, you’ve decided (as I did last month) to dive into wireless networking, frequently referred to as wireless fidelity or Wi-Fi. I confess, hearing about half-price Apple AirPort cards on sale at a few (and I do mean a few) Circuit City stores was the clincher for me. My initial plan was not to spend money on a transmitter to go wireless at home, but rather to make use of my office’s Wi-Fi network when I occasionally brought my laptop with me. It didn’t take more than a few times of doing this before I just had to have a transmitter of my own!
AirPort Base Station or Non-Apple Transmitter?
I could spend a couple of paragraphs arguing the pros and cons of buying and using a third-party transmitter instead of the Apple Base Station, but this article is about the encryption, so I’ll be brief. A third-party transmitter with a built-in multi-port switched router will usually suit your current and future needs better than the Apple Base Station, and cost half as much. Read more about this in Macworld’s April 2002 Base Station review. Also, be sure to choose a device that is configured via a local Web interface and not by Wintel software. Linksys is one such brand, and happens to be the brand I bought.
Important Note: At first, you’ll have to physically connect an Ethernet cable from your computer to the transmitter in order to access its setup screens. This is one of the few drawbacks of using a third-party device; the Base Station software supplied with all new Macs will immediately communicate with a Base Station, meaning you can configure it to access the Internet without ever physically connecting your computer.
Providing Free Broadband Without Even Trying
At this point, we’ll assume you’re happily (and wirelessly) surfing the Net. I bet you weren’t surfing quite so happily however when you stumbled upon the knowledge from the New York Times that there are people out there who run around sniffing out unencrypted Wi-Fi networks and posting their existence to Wi-Fi databases so that they, or anyone else, can camp within range of those transmitters. Voilà! Free wireless broadband! If you want to comment on the ethics and legalities of this, be my guest. I’m not touching that one, but I do want to prevent people from using my bandwidth. As fodder for such a debate, here’s a quote from the aforementioned Times article:
Those who use cable theft as an analogy point to federal law, which prohibits anyone from receiving communications offered over a cable system unless authorized by the cable operator.
But how the law will apply to Wi-Fi technology has not yet been tested. Some legal experts say using stray Wi-Fi signals is like trespassing. Others say the burden of securing the network may lie with its owner, as it does with satellite broadcasters. It is not a crime to tune in to unscrambled satellite programs, but it is illegal to crack the encryption of scrambled broadcasts.
Encryption: AirPort Base Station vs. Other Devices
With Apple’s Base Station, encryption is easily accomplished by setting a passphrase and using that phrase each time your computer’s AirPort card goes to work (or letting your Keychain handle the passphrase for you). An algorithm converts the passphrase into a series of hexadecimal digits to make up a key.

Assigning an Apple Base Station Password
The process is essentially the same for non-Apple computers and transmitters where a protocol known as Wired Equivalent Privacy (WEP) is used. Technically, Apple’s process is also called WEP, although Apple doesn’t seem to use the term as freely as others. Regardless of what you call it, Apple’s algorithm for generating a key from the passphrase is different from the algorithm used by most other transmitters. Consequently, if you use “The quick brown fox jumps over the lazy dog” as a passphrase on a non-Apple transmitter, using the exact same phrase on your Mac will not get you connected. To solve this, you must use an actual key to decrypt the connection instead of a passphrase. There are free utilities to generate hexadecimal keys from passphrases, such as WEP Key Maker. This allows you to memorize a phrase instead of a long hexadecimal key.
At this point, I find myself asking, “Why use a utility? Why not simply type a passphrase in the transmitter’s WEP configuration screen, let it generate the key, then copy that key to use on the Macintosh?” By way of a response, when I experimented with the exact same passphrase typed into WEP Key Maker and my Linksys transmitter, they generated different keys. So much for that theory.
So now I’m asking myself, “Why not just make up a random 10-digit (for 64-bit) or 26-digit (for 128-bit) hexadecimal code, type it into the transmitter’s key field, then also type it in as the password (and save it to the Keychain) when AirPort attempts to connect?” My answer quickly spawned from the unsuccessful experiment from the first question. If it were that easy, someone probably wouldn’t have bothered to write the WEP utility, and since I finally got my encrypted wireless connection running, I’m not going to mess around with it! If you know something about this, by all means, tell us about it.
Encryption Steps
So, unless someone identifies a way to decrypt the connection without using the utility, here’s what you need to do. First, launch the WEP utility and type a passphrase into the space provided. Choose between 64-bit or 128-bit encryption, then click the Make Key button. Highlight and copy the Hex Key, and you’re done with the WEP utility.
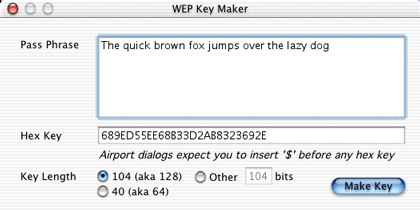
Generating a Hex Key with WEP Key Maker
Open the configuration screen of your transmitter and go to the WEP settings. Remember, you’ll have to be physically connected with an Ethernet cable for this step, or using another computer that is physically connected. Ignore the field where you would type a passphrase. Select the same level of encryption that you chose in the WEP utility and paste the key into the WEP Key field. If you see multiple key fields, use the first one and make sure it’s selected. Confirm that encrypted connections are enabled, then save/apply your settings. You’re now done with the transmitter configuration page.
Finally (assuming your network settings are correct—probably simply set for DHCP), turn on your Mac’s AirPort connection and select the name of the network you want to use. This name is defined in your transmitter’s setup screens and is probably labeled ESSID. You should then be asked for a password, where there’ll be an option to add the password to your Keychain. Use the same hex key for the password, except prefixed by a $ symbol. The dollar sign apparently tells your Mac to not generate a key from what you type since you’re manually entering the key itself. Note that you will not likely be able to paste the hex key from your clipboard into the password field. If not, just paste it into a text window where you can see both it and the AirPort password field, and type it in manually.
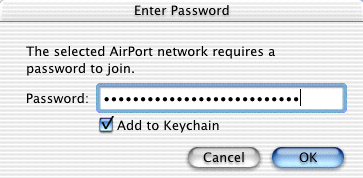
Remember to precede the WEP key with a dollar sign, and consider using your Keychain so you won’t have to type this in again.
One Last Consideration
As a postscript to all of this, allow me to share one other tidbit that I learned while gathering information for this article. I was informed that using encryption will cut the bandwidth of your wireless connection by roughly half. At first, I thought, “That’s impossible. I’m using encryption and I get the same speeds as when I still ran an Ethernet cable.” But then I realized that broadband bandwidth (generally between 512 Kbps and 2 Mbps) is vastly slower than the throughput Wi-Fi transmitters are capable of (usually around 11 Mbps under ideal conditions). So, if you’re only using Wi-Fi for Internet access, this slowdown won’t affect you in the least. However, if you intend to transfer large chunks of data between local computers over a Wi-Fi network, you may want to consider an alternate form of security.
Also in This Series
- Give Alert Sounds a Little Personality · March 2012
- Create Your Own iPhone Ringtones · February 2012
- Create Your Own Homemade Audio Book · December 2011
- Upgrade to Lion Painlessly · August 2011
- Make the Most of TextEdit · July 2011
- Using the Free Disk Utility on Your Mac · May 2011
- Making Use of QuickTime X · March 2011
- Making the Most of What’s Already on Your Mac · February 2011
- Making the Most of What’s Already on Your Mac · January 2011
- Complete Archive
Reader Comments (72)
Thanks for the article. I just picked up an AirPort card for my iBook and an SMC base. I had no idea how to get the WEP encryption working between them.
Your page was the only simple step-by-step how-to I could find.
Very nice!
By the way, today I decided (for reasons that have nothing to do with this article) to make some adjustments to my router's settings, which included disabling DHCP access. I set up my two computers with manual/static TCP settings. My dialog with colleagues indicates that 1) not having to handle DHCP networking may allow for more efficient communication within the LAN, and 2) not freely handing out LAN IPs just adds another level (albeit a thin level) of security. That level is bolstered, somewhat, if you set up the router to not use the common 192.168.1.x IP set and use 192.something.else.x instead. So, here at home, I'm obviously not in a situation where there are tons of computers needing LAN access that I'd have to manage IPs for (DHCP automates this) and, in the rare case when I get a visitor with a Wi-Fi-equipped laptop, it takes all of 15 seconds, usually, to tell him/her my LAN network settings rather than just saying "use DHCP." Big whup.
Anyhow, the point I really wanted to make was ... while making the configuration changes, it occurred to me that my note, above, that stated you would, at first, need to have your computer physically connected to the wireless router to set it up may not be a requirement after all. Generally, wireless routers, out of the box, are factory-configured with WEP disabled and with DHCP enabled. It seems to me, now, that I should be able to obtain a brand new router, plug it into a power outlet, turn on AirPort on my laptop, select the network which will not be encrypted at this point, connect to the configuration pages with my laptop by opening http://192.168.1.1/, make adjustments (if needed—often, none are needed) to set up the router to use your incoming WAN (usually broadband) connection, and voila ... you're surfing!
Granted, if you choose to tinker with the LAN address settings, you may experience various drops of Wi-Fi signal and/or WAN connectivity, but if you don't mind reconnecting to the Wi-Fi signal once or more and/or reloading a web page or two, I think you should still be able to get everything set up without plugging an ethernet cable into your computer.
If someone can confirm/deny this in a comment here, please enlighten us all!
Not knowing any better when setting up my home network, this is exactly what I did. I have D-Link 614+ Wi-Fi router, and it worked fine on my PowerBook G3 Firewire. However, it does not work on my PowerBook G4, which will only connect to the D-Link if WEP is disabled. I have no idea why this is, as I have identical system software installed on both (OS 9.2.2 at this point), and have checked and rechecked to make sure that I'm using the same password 50 times. Any help would be very much appreciated. Thanks.
HOWEVER, the next time I reboot, I am prompted to enter the password to connect. :|
To test: I typed in the $HEX and added to my keychain, I could see the entry in the Keychain Acess utility. But as soon as I tried to connect again (after a reboot), I watched as the keychain entry disappeared! I was then prompted for my password. :(
Any ideas?
I checked my Keychain and I'll share how mine is set up so you can try to match it and see if it works.
There are 2 items related to the Wi-Fi connection. The first is named "AirPort Network Password" and the kind is "application password." It's attributes show the "Account" field as being my wireless router's name (the ESSID I mentioned in my article). The Access Control tab (actually to my suprise) is set for "Confirm before allowing access" but in the list of "always allow" apps, there are three (weird, huh?) listings for /System/Library/CoreServices/SystemUIServer and a fourth listing that is /Applications/Utilities/Keychain Access
The second item in my Keychain list is the same name as my router's ESSID, and the kind is "AirPort network password." Its attributes also show "Account" as my ESSID. The Access Control tab is set for "Always allow access to this item."
One other thing ... here's something I did recently that solved another problem I had with recurring password requests, though I've never had the problem with my wireless connection. In the Keychain Access app, go to the Edit menu and select "..user.." settings (where "..user.." is your short login name). Mine had been set to lock after 1 minute of inactivity. If your computer is pretty secure you can turn that off or, as I did, set it a little higher, like 10 minutes.
Check all that out, and if you still have trouble, e-mail me directly and I'll see if any other ATPM staff have some ideas.
While it would be nice if Apple had information about using the dollar sign character, I can sort of understand why they don't. Naturally, Apple is going to hope you'll use their products. If you do so, using the dollar sign character is irrelevant. What motivation do they have for explaining something that is only helpful for a competitor's product?
I read your article on WAP keys for Apple and non-Apple systems. For a second, I thought I might have solved my problem. Alas, I did not.
Here is the problem: I am using a Linksys wireless access point router with 4-port switch (BEFW11S4 V2) on a Windows 98 V2 network. My wife just purchased a spiffy new G4 PowerBook with an AirPort card preinstalled directly by Apple. I can get her to connect to the wireless access point if WEP is DISABLED on the Linksys box. There's no way can I get her to connect with WEP ENABLED on the Linksys box.
I have made certain that all updates/upgrades/patches have been done to both the Linksys box and the PowerBook.
I have entered HEX key data with the $ sign preceding the key data. I have even downloaded the key maker application from Chally that you mentioned and generated the key on the PowerBook, then hand keyed the same key into the Linksys.
Still no go! Could you point me in the right direction? I feel like I have tried everything and know that I must be doing something wrong as the folks at Apple swear that the Linksys box works with their PowerBook and that it was a better choice, given the Windows stuff already here at home. Thanks very much.
Michael
Here is exactly how I would set up a Linksys and Mac OS X if I were doing it from scratch:
That should take care of it. You should be able to copy the hex key out of the Linksys web configuration pages, and use that on your PC boxes as well, if they are using a wireless connection.
Most vendors' WEP implementations support 4 encryption keys. The Wi-Fi software (either on the WAP or the PC Card driver) lets you specify 4 different keys. Plus, you have to select which of the 4 keys is used for encrypting the transmitted (outbound) traffic. In order to establish a secure connection, each end (WAP and MS) must share each other's keys that are being used.
So, if the WAP is using key #1 for transmitting, the mobile station must have the same key loaded as key #1. If the mobile station is using key #3 to transmit, the WAP must have the same key loaded as its key #3. It is not required that all mobile stations associated with an AP use the same key # for transmitting, but if the AP is going to be able to decode the packets, it must be configured with the same encryption keys in each of the 4 slots that are being used.
The WEP standard stipulates that each transmitted packet carries with it the key # that was used to encrypt the packet. At the receiving end, the driver looks at the key # (which is transmitted in cleartext as 1,2,3, or 4). Then, it grabs the corresponding encryption key from the designated slot and uses it to decrypt the packet. So, if the mobile station is using key #2 to encrypt the transmitted packets, the AP needs to have the same key loaded in slot #2.
Thus, it is quite possible that two different key strings are being used for encrypting the upstream and downstream transmission. Each end gets to independently specify which key # is used for encrypting its outbound traffic. Each end tells the other which key # is being used, and the receiving end then has to have shared knowledge of the 40-bit or 106-bit key for decryption.
There is a good article in Acrobat format that explains the rationale behind this 4-key architecture and how is is intended to be used for key rotation.
The problem with Apple's AirPort implementation is that Steve et al chose to implement only key #1. Thus, the AP must explicitly use key #1 for transmission. If the AP is not using key #1, AirPort users are out of luck.
If an AirPort user happens to walk into a Wi-Fi environment that is using a 3rd party base station set to encrypt its transmitted traffic with keys 2,3 or 4, the AirPort can't decrypt it, even if it knows the full hex encryption key.
This constraint/limitation pertains to OS 9 AirPort software. I have not had the pleasure of using OS X and do not know if Apple fixed their AirPort driver to accommodate multiple keys.
I also verified that you have to use a "$" when entering the key under Mac OS 9, but no "$" when running Mac OS X 10.2.2.
And yes, as I mentioned in a comment above, with Jaguar, you no longer need the "$" character since there is now a pull down menu to choose 64-bit ASCII, 128-bit hex, 64-bit ASCII, or 128-bit hex. Naturally, you'd use one of the "hex" selections, depending on the level of encryption.
I can attach fine without encryption.
Does anyone have any ideas on how I could connect, or am I stuck in the situation described by David C.?
One thing that did not work out the way I had anticipated was the setting under System Preferences/Network where you can set the AirPort settings for finding the network after restart or wake from sleep. If I tried to identify the specific network and input the password as had worked elsewhere, this adversely affected accessing the network after cold bootup. Instead, if I identify "Join most recent available network" and place a check in the box to "remember network password," it works fine under all conditions. I don't know why the former approach doesn't work, but since there is only one network here at home, it is OK for me.
Andrew
It doesn't matter which direction you're going, the fact that different algorithms are used for the passphrase/hex key conversion still applies.
But as I indicated in an earlier comment, you don't have to use the WEP Key Maker if you don't want to. You can just invent your own hex key. The only benefit I now see for using the utility is so you can have a passphrase to remember instead of the hex key. The WEP Key Maker converts the passphrase into hex for you and is consistent.
I tried your method of turning on WEP with no success at all. The menu icon on desktop changed from active to an arrow pointing upwards and no activity was indicated at all.
I'm still confused and somewhat disappointed that the Mac didn't hook up to my existing network. I know the wireless part works since I am able to access network wirelessly with a Dell Inspiron 3800 using a Linksys wireless USB adapter--a WUSB11.
Any help would be appreciated.
Tom
selecting 'password' and using the $, but that doesn't help either. Michael, Matthew, Tom--I didn't see any response from you indicating whether your issues were resolved. Did you eventually find anything else out? Can anyone else suggest anything else to try?
The password I set up on the AirPort is working fine with my PowerBook, but not with the Dell PC.
It's either a simple problem the PC is having with the password or something more complicated with the encryption. I'm afraid most of the info on this page is a bit above my head. Is there anyone who could walk me through diagnosing the problem in simple language?
I'd really appreciate it!
Thanks.
Preceding a hexadecimal string of characters sent to an Apple device, you may have to use the dollar sign: $
Preceding a hexadecimal string of characters sent to a non-Apple device, you may have to use a zero with a small x, like this: 0x [instead of the dollar sign].
Example; to an Apple device [no spaces, but I include them here, in order to make it easier to read the string]: $ 34 6e 53 73 4e 3b 94 49 1d 0c 11 2b 44
Example; to a non-Apple device [no spaces, but I include them here, in order to make it easier to read the string]: 0x 34 6e 53 73 4e 3b 94 49 1d 0c 11 2b 44
I'm running 10.3.3 with all the latest updates as of this writing.
In the router config screen, under the Wireless Security tab, I've selected WEP and 128 bits 26 hex digits. I typed a simple passphrase (meatball) and clicked the "generate" button. Presto, a 26 digit hex key was created.
On my iBook, I tried to join my SSID network and no matter what I tried typing in, it would not accept it "there was an error connecting to..." I found this web site and tried a few things, none of them successful. E.g. in the Airport dialog box on my iBook, if I choose the 128 bit 26 hex option, it does not allow me to type a $. Just boops at me. But if I type in the full 26 bit hex key (case insensitive) it accepts it and logs me in without a hitch!
I did *NOT* select the "add to keychain" option -- but after sleeping the iBook, it re-found the network right away! It was only after restarting the machine that I had to re-enter the hex key. But then I changed the passphrase, got a new key, tried it all again, and this time (again, without checking the "remember password" box) it remembered and connected fine after both a sleep and a restart!
I'm not sure why that is happening. Hmph.
I'm also interested in WAP. But here are a couple basic security assumptions. Please tell me if I am off base.
(1) If I set up the MAC address filter, no one can access my WiFi. They may be able to sniff it, but they can't hijack my WiFi and surf, etc.
(2) If I disable SSID broadcasting, that makes their sniffing a bit more difficult, since it is only the serious sniffers who would be able to find it?
(3) With the above two in place, but without using WEP (WAP, etc) then -- even if they can't hijack my WiFi and surf -- someone can sniff my WiFi transmissions between iBook and router and steal my info?
(4) From what I've read, WAP is better than WEP (better = easier and more secure) but I have not been able to find info on configuring WAP. Any help?
~ Keith
I'll have to let someone else possibly chime in about remembering the password. I wouldn't have thought the key would be remembered after a restart. Perhaps Networking remembers it so long as you don't select a different type of network.
Regarding MAC address filters, it's still good to use encryption as well as address filtering. I haven't a clue how to do it, but I know it is possible to spoof a MAC address. If they sit out and packet sniff your Wi-Fi network long enough, the MAC address of a machine that is using the network can be learned and they are able to trick your wireless router into thinking their machine has a valid MAC address.
Re: disabling SSID, that would prevent casual drive-bys from seeing it, but it wouldn't deter anyone serious about finding networks.
For #3, if you read the previous two paragraphs, you now have the answer to this question.
And for #4, you mean WPA, not WAP. WAP stands for wireless access point, and your wireless router is a WAP.
WPA, however, stands for Wi-Fi protected access and it is, indeed, better then WEP. The problem is, the older Linksys routers don't support it. I have the same wireless router as you (except mine is a v2) and I've not found any firmware updates that add WPA to it. You will probably have to purchase a newer router to get WPA encryption. The newer routers will be 802.11g and will let you take full advantage of AirPort Extreme's faster speed. It won't increase your internet speed, but it will make networking between your home computers faster when transferring to or from your laptop.
If you do manage to start using WPA, don't get terribly complacent about its security. It probably can be cracked, as well, but may require many days or weeks worth of someone sitting in range of your router and sniffing packets before they'd be able to crack it. You simply have to be pro-active about securing a wireless network. This means using a complicated keyword to generate a hex key, changing your key often, setting up MAC filtering, and even things like disabling DHCP and hard-assigning IP addresses to all your computers. I even changed my default IP range so it's not using Linksys' common set of 192.168.65.x.
My router Admin page does allow me to choose WPA. My "Security Mode" choices are:
WPA Pre-Shared Key
WPA RADIUS
RADIUS
WEP
If I choose WPA Pre-Shared Key (since I have no separate RADIUS server to run authentication stuff), my choices change to suit. Now I can select:
WPA Algorithms (TKIP is my only choice, but from what I've read, it is what I would want to choose anyway)
WPA Shared Key (only accepts entries over a certain number of characters)
Group Key Renewal (default is 3600) seconds.
When I choose this method, and select a key (of acceptable length) and then choose "save" -- then try to re-access my WiFi, the WPA key is not allowed -- I get the dreaded "there was an error connecting to the network iMajor's WiFi"... whether I use a preceding $ or a preceding 0x or put it in quotes, etc.
What do you think?
I have posts on Apple's Discussion forums as well, as of today -- we'll see what I find out from there!
Another quick note--I fooled around a bit more with the "remember this password" box. I selected it and then looked in keychain access -- no entry there!
Maybe Internet Connect's .plist file keeps the WEP and WPA passwords somehow? I dunno.
Just in case, I've saved a small StickyBrain note file with the 26 hex WEP key. And I'll probably put it in my Palm too.
~ Keith
http://www.wi-fi.com
And specifically:
http://www.wi-fi.com/OpenSection/protected_access.asp
Thanks for all your help Lee!
~ Keith
Go back to PC turn on WEP - set it up, enter password and keys. apply now - woot everything works dandy.
GO back to Mac select network to join, hit ok.... it joins.. I shows a connection. BUT it isnt connected. Safari "you are not connected to the internet"
I look at the airport and it shows me a connection.. hmm so I try to change the connection to secure because I assume somehow it has connected but its not secure. Turn on WEP for the airport card. No nothing on the mac will connect. It says I have used a wrong password. And yes, I did enter the $
Confused...
But if AirPort is showing that you have a connection, but Safari isn't loading any pages, I'm a little stumped. Can you do other internet activity such as checking e-mail or using an instant message client. If so, I'm wondering if you need to plug in DNS addresses in your Networking preference pane...whichever addresses your internet provider advises you to use.
Also, which operating system version are you using?
40/64 bit keys use 10 hexadecimal characters and 104/128 bit keys use 26 characters. That info may also help you identify which type of encryption your router is using. Enter the key with no spaces between any part of the key and, naturally, make triple certain you're typing in the exact same key.
Check and see if other applications besides web browsing will work. If so, your problem is DNS issues. To solve this, you'll need to identify the DNS addresses that your internet provider advises customers to use and enter those into your iBook's Networking preferences. Usually, this information is supposed to automatically come down via DHCP, but sometimes you have to enter it manually.
This seems to be a bit of cheap engineering on the part of Apple OSX team.
Can someone walk me on how to get the internet on my ibook?
Thanks :-)
Can someone walk me on how to connect the 2?
I don't know what to do with this, cause I already tried to use the WEP encryption method but it didn't work with that one either. Now in his computer the only method encryption that the computer supports is WEP. Is it a problem with the wireless network card his is using or with the drivers for it????
Having said that, ATPM focuses on Macintosh subjects and support so there's very little our staff can do to assist.
Judging from your comments, you answered your own question. If the Base Station is using WPA and the Windows machine's card only supports WEP, you're out of luck. You'll have to either upgrade the card to one that supports WPA encryption (unless a simple driver update will do that), or run your Base Station in the less-secure WEP mode. Any further help on the Windows machine is unavailable on this forum.
I am trying to get my iBook running OS X 10.1 to connect securely (using WEP 128-bit option)to a DLink DI-524 wireless router. Connecting unsecured is no problem. I have tried using the key maker procedure with prefix "$", but no luck. It still doesn't accept the hexadecimal code provided. I have skimmed thru the above threads, but don't think there are any other tips other than using "0x" prefix, which also didn't work. Have I missed something... ? Any other tips or advise much appreciated.
Having said that, there were two different versions of the original AirPort card prior to the 802.11g-enabled AirPort Extreme. The first version did not support 128-bit WEP—only 40-bit. If you have such a card, you're out of luck unless you take your DLink down to 40-bit as well.
Otherwise, if you can find one (eBay), you could get the 128-bit AirPort card and swap it out in your iBook.
As for security, it has nothing to do with which card you have. There were two strengths of WEP encryption but both are not spectacularly secure. The newer, stronger encryption is known as WPA and can be used on both the original 802.11b AirPort and the 802.11g AirPort Extreme. You simply need later versions of Mac OS X and updated AirPort firmware to support WPA—as well as a wireless router that is WPA-compatible. I'm pretty sure that Panther (OS X 10.3.x) supports WPA, just not sure how high a version for "x' is required.
Using his passphrase to generate a hexidecimal number in 128-bit WEP mode, I was able to log in and everything worked fine, internet included. And then the next day it stopped working and I could only log onto the network, with no router address and no internet connection. Odd.
As for the Mac saving the passwords, as some had questions about above: there are two places the password can be saved. The first is in the keychain and the second is in the Network Preference Pane. If you click on "configure," you'll note that there is probably a list of previously-connected networks, which are automatically saved each time you connect to a network. If you want to turn this feature off, click on "Options" and uncheck the correct option.
Anyone have any suggestions about how to type connect to the internet on this darned Linksys? I've had no problems with my own router at home (Netgear), or at work, either.
I've been trying to set the WEP on my Linksys BEFW11S4 for over a year! Every time I hunted the web for help tips, I just ended up being too frustrated and quit.
Thanks again for posting this article...
-Christopher
But, our frustration is over. Apple did get their act together. A firmware update to the wireless software (as well as being automatically included in OS X 10.3) updated the algorithm for WEP key generation. You can now use the standard WEP passphrase. Consequently, the above article that I wrote five years ago is now obsolete—as is the WEP Key Maker software.
I was under the impression that at least at that time, Apple did not support WPA with 10.3, if this has changed I would like to bolster my security setings just for the hell of it.
Does the updated 10.3 support all higher levels of WPA that linksys router has?
These updates, however, should have appeared in the standard round of Software Updates, so be sure to check there. If you are caught up on all updates (and you definitely should be up to 10.3.9 if you can't go to 10.4.x), then you probably already have WPA support.
Thanks, Andy
I've got an iMac Core2Duo under MacOS X 10.4.9, and I do try to share my ethernet DSL connexion with a an IBM Thinkpad laptop PC, using the in-board airport connexion of the mac.
So, after having turned aiport on I go to the "sharing" control panel, set up the airport options and start internet sharing.
If I leave the network I've just created "open", everything works fine.
But if I want to activate the encryption the Mac does only know WEP-40 and WEP-128.
Whatever the one I choose, then the PC always says it can't connect.
I've tried ascii password. I even tried to set up the airport password as stated in Apple documents (Example of 40-bit: $1234abcdef
Example of 128-bit: $12345678901234567890abcdef) while checking the "hex" choice on the IBM.
Also, I took care of specifying key 1 on the IBM side, but alas, it still doesn't want to connect.
Does Anybody have got an idea ?
btw, some config infos :
- the PC is a Thinkpad T41 under Windows XP Pro, centrino platform in 802.11b
- all the configuration process I describe worked perfectly with my old G4 (802.11b airport card) under 10.4.9 or 10.4.10. Why it doesn't work on an intel iMac, well I don't know...heeeelp !
But the passphrase should be working. As I've said in earlier comments on this page, Apple wisely changed to use the same algorithm for generating keys as everyone else, so a passphrase that is set up for a router should work fine on the Mac.
Thanks for your answer.
But, even with Tiger there is no "hex" poplist when you want to share your DSL internet connection using your Mac's internal aiport card. There's only WEP encryption, it's a a shame. You have only a checkbox (crypted or not), and a poplist to choose between 40-bit or 128-bit (ironically, not "40 and 104", nor "64 and 128" ! :-)
The "$" technique still works, as I have tested on a Tiger G4.
btw, before sending I had read all the articles (and had noticed the article was out of date :-)
Any ideas are welcomed.
Add A Comment